As with any high-stakes event, elections have become a prime target for cybercriminals seeking to exploit public trust through impersonation, misinformation, and scams. CSC’s comprehensive research about the 2024 U.S. Election reveals the alarming role of dormant domains, which have the potential to be exploited for launching cyber attacks against political campaigns, organizations, and constituents.
CSC researched election-themed domain registrations from January 2023 to September 2024 and observed 59,000 unique domain names that were not owned by the candidates, political parties, or voting organizations. These third-party domain registrations spiked considerably in the wake of key events during the election, as seen in figure 1.
Figure 1: New domain registrations from July 1, 2024, to August 16, 2024
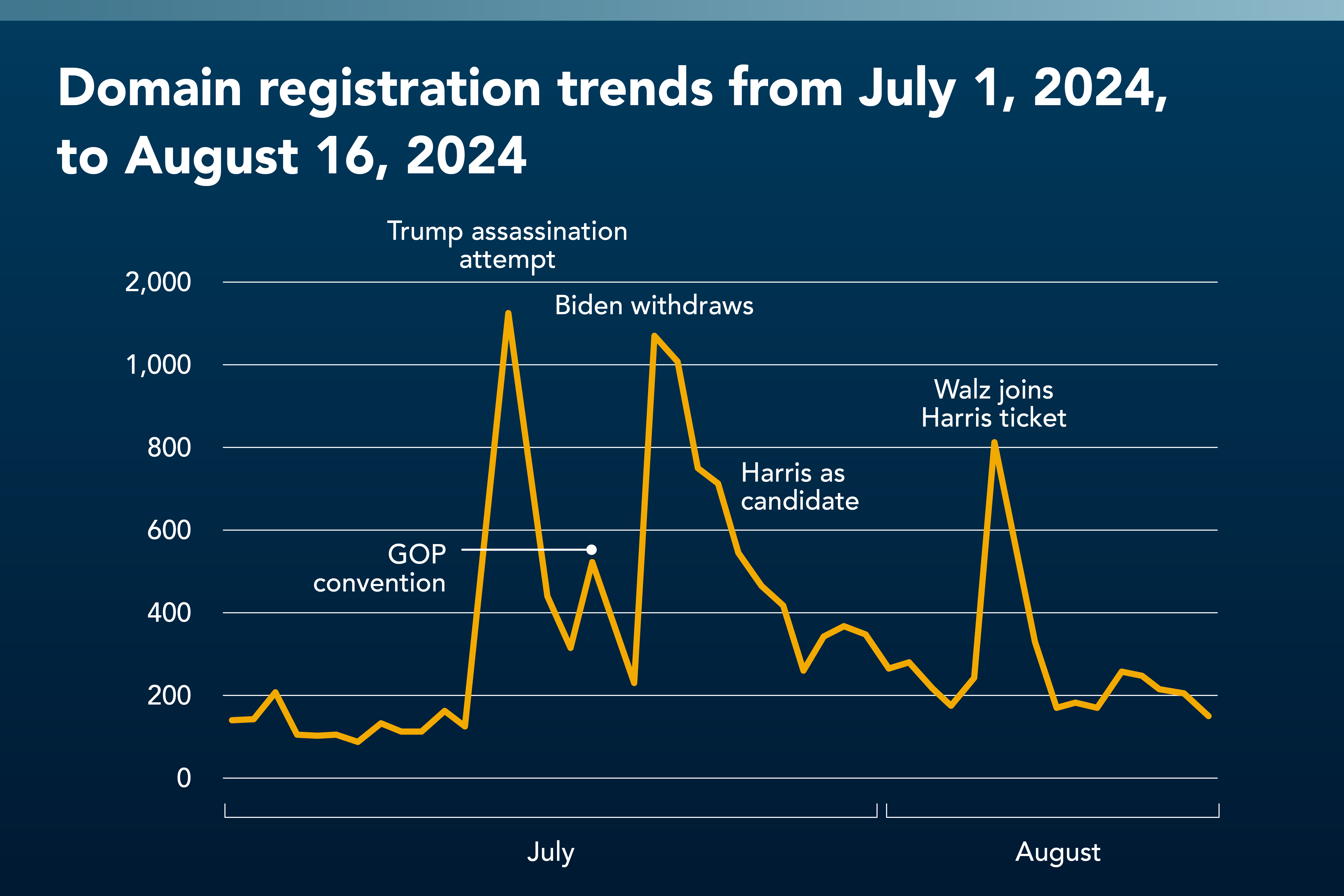
Out of the 59,000 domains, 40,157 domains were still registered in September 2024. Out of this new total, we had found that more than 7,000 could be classified as “dormant domains.”
How to assess risk with third-party domains
Dormant domains are inactive, meaning if you attempt to type in their URL, you won’t reach a website, but likely an error message. The issue that may arise is when one of these dormant domains is suddenly activated for malicious purposes, such as a phishing or malware attack. Bad actors could make these dormant domains active during or immediately after Election Day, with the goal of seeding disinformation and distrust in election results.
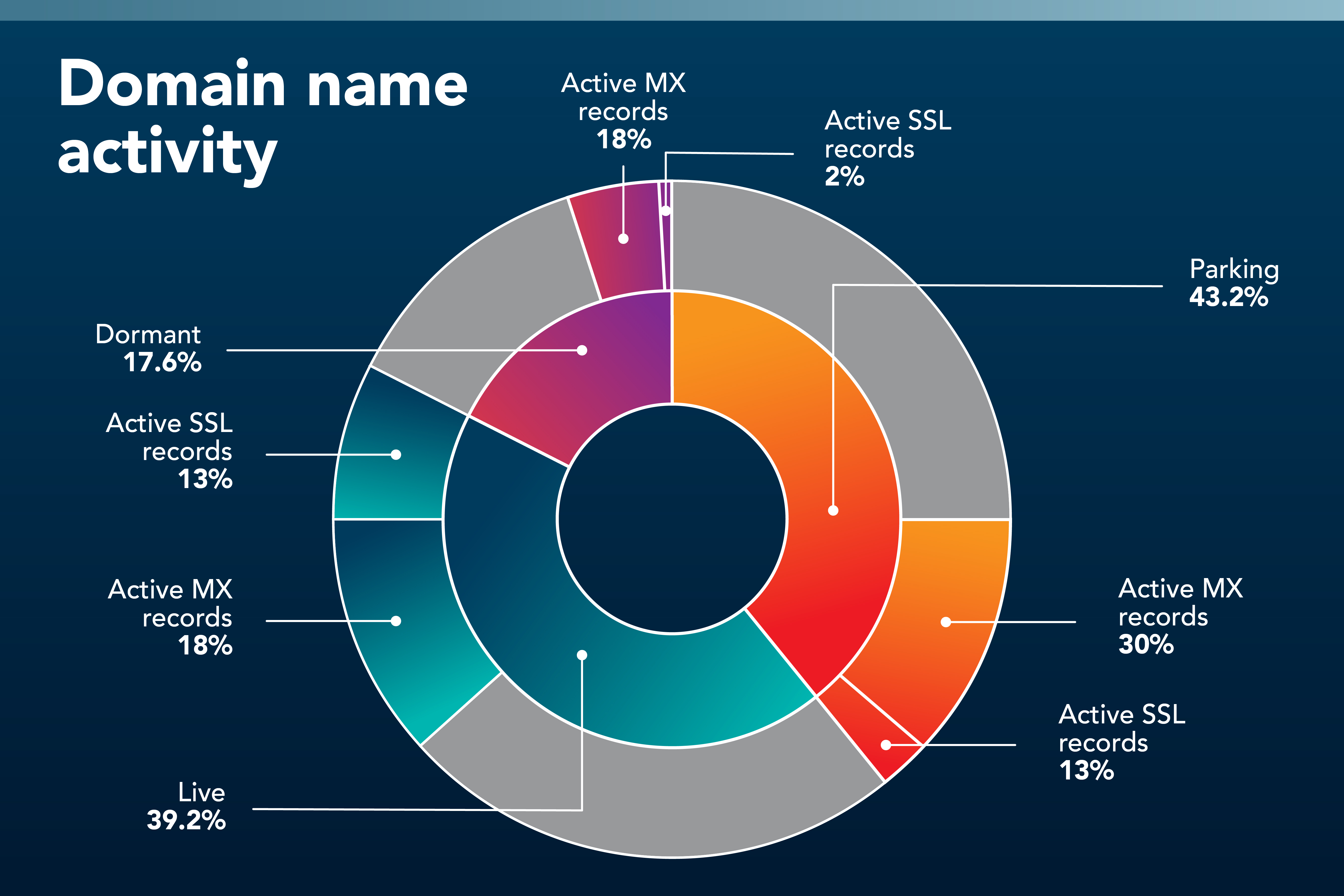
Aside from dormant domains, about 43% of the domains were “parked,” which means they do resolve to live content, but don’t present a typical online user experience. You’ll usually see a “coming soon” page or a pay-per-click page. Third parties may hold parked domains with the purpose of reselling them at a higher price or using them for a future business investment.
To make an educated guess about the motive behind registering a domain, our research team looked at several clues based on the domain’s infrastructure, such as their secure sockets layer (SSL) certificates, mail exchange (MX) records, proxy services, and hosting providers.
For example, a domain with active SSL certificates and MX records suggests some level of intention towards use. Below is a chart of the 40,000+ domains that were still registered and their infrastructure activity trends.
Figure 2: Domain name activity of live, parked, and dormant registered domains
Trendspotting: Fake domains during an election
Many spoofed domains use words related to a brand or topic that may bring traffic, such as the election or its candidates, combined with prefixes and suffixes. Prefixes that appear before the domain in a URL were wide ranging, such as, “the,” “vote,” “president,” “2024,” and “MAGA.”
Common suffixes that appear after the domain names and are also known as top-level domains included “2024,” “sol,” “coin,” “merch,” and “store.” Notably, cryptocurrency has become a popular keyword theme. For example, SOL is the abbreviated name for Solana, a type of cryptocurrency.
Another technique is typosquatting, which tricks visitors who accidentally mistype their intended destination online. We also saw that about half of these domains were issued SSL certificates by a free and open-source certificate authority (CA). Working with this type of CA would lower the barriers for cybercriminals trying to set up fake websites and emails. Additionally, 66.3% of the domain registrars were the same three consumer-grade companies.
Examples of potentially fraudulent election websites
If dormant domains were to be unleashed, they could become fraudulent websites. Below are a few examples of what a harmful site could look like.
doonaldjtrump.com
Note the misspelled name. A donation link went to another fake domain (pay.coingaete.com). When we investigated, it held an active MX record and an SSL issued by a free and open-source certificate authority.
kamala.ltd
When we visited the site, the browser flashed a warning that the security certificate expired 163 days ago. But the domain had active text (TXT), MX, domain-based message authentication, reporting, and conformance (DMARC), and sender policy framework (SPF) records associated with it, which indicates an intent to use.
donaldjtrumpcampaign.us
Registered at Registrar.eu (based in Europe), this appeared to be a fake donation site, with a link to a cryptocurrency account instead of an official WinRed website. It also had active MX records and an SSL from a free and open-source certificate authority.
Key takeaways for brand owners
Criminals won’t think twice about abusing your brand for deceptive purposes, so maintaining a domain portfolio and protecting your digital assets should be top business priorities.
Here are some recommendations to help you stay secure:
- Use a monitoring system with artificial intelligence (AI) and machine learning (ML). While bad actors are using AI and ML to increase the potency and frequency of cyber attacks, you can use the same technology to monitor for threats on the internet, such as third-party domain registrations with keywords connected to your brand. Your platform should also ideally alert you to any vulnerabilities in your own domain infrastructure.
- Work with 24x7x365 enforcement. Cyber threats warrant swift action once they’re detected. An enforcement firm can provide you with the ability to quickly take down harmful vectors such as phishing, typosquatting, and counterfeit sites.
- Partner with an enterprise-class domain registrar. A registrar of this class can provide your organization with comprehensive offerings for your domain management, security, and strategy needs.
What’s lurking in the online landscape that could take your business by surprise? Learn more by speaking with an enterprise-class registrar to spot threats and risks.
