When major events like the Super Bowl are on the horizon, cybercriminals exploit public trust by creating fraudulent domains for fake betting sites, phishing, and malware distribution. CSC’s research into top online sportsbooks highlights the hidden risks of dormant domains, which, though inactive, can quickly be repurposed for cyber attacks. Overlooked yet dangerous, these domains play a key role in impersonation, misinformation, and scams targeting event-driven traffic, underscoring the need for continuous monitoring of lookalike, dropped, re-registered, and newly registered domains.
Key findings and highlights
Between January 1, 2023, and December 24, 2024, CSC analyzed the behavior of third-party domains targeting major online betting websites. Our research identified 5,000 unique domain registrations mimicking well-known sportsbooks. Due to domain expirations, about 3,400 of these domains remained active as of December 24.
Identifying domain risks: Dormant, parked, and live unauthorized sites
Understanding how third parties register and use betting-related domains is key to assessing security risks. Some domains remain dormant, others are parked with placeholder content, and some resolve to live websites—each category presenting different threats. Among the 3,400 third-party domains that were still registered, we found the following trends.
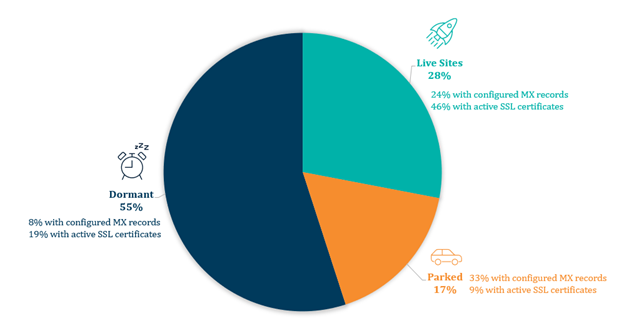
- Dormant domains (55%) – While currently inactive, these domains can be activated at any time for phishing, malware distribution, or impersonation schemes. Of these dormant domains, 8% have mail exchange (MX) records configured, indicating potential for email phishing, and 19% have valid secure sockets layer (SSL) certificates, which can lend credibility to fraudulent sites.
- Parked domains (17%) – These domains display placeholder content or ads but contain well-known betting brand names, suggesting that may be reserved for traffic diversion or future misuse.
- Live unauthorized site (28%) – These domains actively host live content, with 13 attracting enough traffic to rank among the top one million websites globally—despite no verified connection to the original betting brands.
Figure 1. Domain name activity
Common infrastructure in third-party betting domains: Registrars, SSL providers, and keyword trends
Threat actors don’t always rely on obscure or offshore infrastructure—many use mainstream domain registrars and SSL providers to lend legitimacy to their operations. While some third-party domains are registered through lesser-known services, others use well-established registrars and encryption providers, making them harder to distinguish from genuine sites.
The table below highlights the most frequently used domain registrars and SSL providers associated with third-party domains, as well as the top keywords observed in these registrations. Understanding these patterns can help businesses anticipate emerging threats and refine their security strategies.
| Domain registrars used (% of overall registrations) | SSL providers used | Top keywords observed |
| GoDaddy.com, LLC 21% NameCheap, Inc. 17% Realtime Register 7% Gname.com Pte. Ltd 7% Dynadot, LLC 5% | Google and Let’s Encrypt made up 94% of SSL certificates to these sites: Google 52% Let’s Encrypt 42% | Prefixes: indo, aia, ufa, royal, www, slot, SBO, and pix Suffixes: s, z, slot, a, x, sports, sportsnetwork, and casino There were 453 different prefix and 867 suffix keywords used across the domains. |
The extensive variety of keywords used in third-party domain registrations mimicking top sportsbooks demonstrates the sheer creativity behind these naming tactics. Simple variations—such as adding an “s’” or “z” to a brand name—highlight how easily domains can be manipulated to appear credible. With 453 different prefixes and 867 unique suffixes identified, the number of possible deceptive domain combinations is virtually limitless.
The overlooked risks of domain impersonation
Our research shows that at any given time, less than 5% of third-party domains actively engage in fraudulent behavior. However, this figure vastly underestimates the true scale of domain fraud due to the limitations of point-in-time analysis. A domain’s status is not static—what appears harmless today can quickly shift into a vehicle for phishing, malware distribution, or brand impersonation.
In the betting domain ecosystem, 72% of domains analyzed were classified as inactive or parked, but this doesn’t mean they’re benign. Many of these domains can be reactivated at any moment for malicious purposes. By continuously monitoring key risk indicators—such as hosting infrastructure, SSL activation, and email configurations—organizations can detect early warning signs and mitigate risks before they escalate.
Managing domain risks with CSC
To stay ahead of domain-based threats, businesses need effective monitoring and enforcement strategies. CSC’S 3D Domain Security and Enforcement provides a comprehensive approach to tracking unapproved domain registrations and mitigating risks before they escalate. Through continuous monitoring and proactive enforcement, organizations can protect their brands from domain abuse and cyber threats. Learn more today.
