
By Sue Watts, Global Marketing Team Leader Share this post 


Domain names, domain name systems (DNS), and digital certificates are fundamental components of the most important applications that enable your company to conduct business—including your website, email, voice over IP, and more. However, these vital applications are being attacked with an increasingly high level of sophistication and severity.
When these assets are compromised, criminals can redirect websites for financial gain, intercept email to conduct espionage, and even harvest credentials to breach your network. This can have a serious impact on your company’s revenue and reputation, costing you customers and exposing your company to significant financial penalties through the EU’s General Data Protection Regulation (GDPR) and other policies like it.
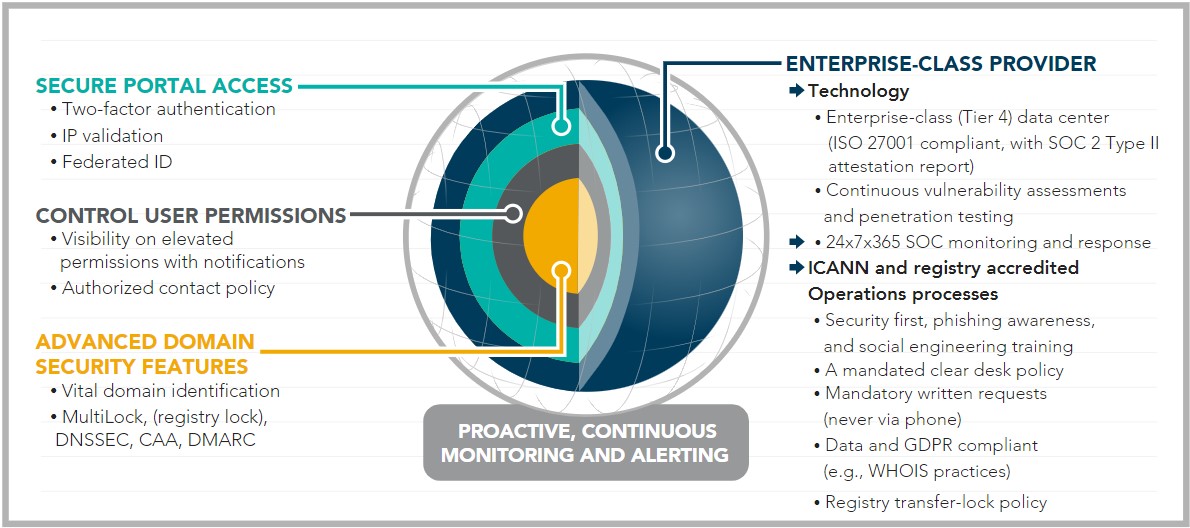
Our defense-in-depth approach for domain and DNS security offers four layers of security to provide the highest level of threat mitigation.
1. Be sure you’re working with an enterprise-class provider
While anyone can say they offer services that meet the needs of today’s global corporations, the onus is on you to do the homework to understand the differences between third-party providers. Companies need to understand how their choice of provider fits into decisions made about their organization’s overall security posture, along with concerns about IP infringement and trademark law.
When it comes to the domain ecosystem, choice of domain registrar can impact colleagues responsible for cyber security and IT, as well as legal (general counsel), risk, and compliance (chief risk officer)—because it has a major impact on cyber security, phishing attacks and online fraud, and brand abuse. To manage a company’s domain name portfolio, you need to work with a provider that has invested in protecting its own systems.
With all of the cyber security threats today, not only does your domain name registrar need to have the right technology—to protect itself and your company from a data breach—but it also needs best-in-class operations practices that put security at the forefront of its mission, and in how it engages with you. An enterprise-level registrar should have ISO 27001 accredited data centers, SOC 2® compliance, third-party penetration and vulnerability testing. They should conduct regular security tests, including SQL injection and XSS. They should also be Internet Corporation for Assigned Names and Number (ICANN) and registry accredited.
A registrar that’s qualified to serve an enterprise will offer a full accounting of all your domains, DNS, and digital certificate providers. It should provide 24/7/365 support along with cyber security training for its staff, including phishing and social engineering awareness. It’s also important for your registrar to:
- Mandate written requests (never via phone)
- Be data and GDPR compliant (e.g., WHOIS practices)
- Have a registry transfer-lock policy
2. Only work with a registrar that provides secure access to your domain and DNS management systems
The second layer in a defense-in-depth approach for domain security is to ensure your registrar mandates secure access to the domain and DNS management system. Registrars should require two-factor authentication for all their customers. They should also offer IP validation and federated ID so their clients can log into their network and know they have secure authentication into their domain management system.
3. Be certain all your user permissions are controlled and managed
When working with a registrar, it should be able to offer you granular levels of permissions. You need to work with a registrar that lets you have control over who can do what. It should provide you with visibility on elevated permissions, including notifications when changes occur. This is especially important in the event of a cyber attack. If an attacker gets access to a registration system, they’ll either create a new user or change the permissions on an existing user so they can do damage.
4. Use advanced domain security features
The fourth layer of the defense-in-depth approach is to apply advanced security features at the individual domain level. The first thing is to identify your organization’s vital domain names. Typically between 10% and 15% of a company’s domain portfolio are the “crown jewel” domains that power a business, its key websites, applications, and email.
Once you have those names identified, it’s time to apply the proper controls to them. First, there’s registry lock—i.e., locking the domain name at the registry level—which disables automation between a registrar and a registry. This means the DNS can’t be changed without a manual password that must be verified by an authorized contact to unlock the domain name. It’s a highly secure, effective way to make sure that an important domain name’s DNS can’t be changed without the proper authentication.
Another domain security control is DNS security extensions (DNSSEC), which authenticates communication between DNS servers. There are three types of attacks that can happen at the domain and DNS level. One such attack is cache poisoning, where an attacker corrupts the resolver (e.g., the ISP) in the lookup process to return a spoofed IP address, sending users to the wrong place, such as a fraudulent website. Deploying DNSSEC prevents that kind of attack by using digital signatures to validate the authenticity of DNS data.
Third, there is Certificate Authority Authorization (CAA). Once an attacker gets access to a domain name, they can then access the existing digital certificate, or have a new one issued. This allows them to decrypt encrypted information, like virtual private network passwords, email, and so on. CAA allows you to designate a specific certificate authority as the sole issuer of your certificates. If the attacker does not go to that particular certificate authority to get a new certificate, the request will fail. Moreover, an alert will be sent to you to let you know that someone tried to request a new certificate that was outside of your CAA policy. This is a great compliance tool, but it is also a great security layer, alerting you if someone tries to issue a certificate on one of your key domain names.
The last advanced security protocol to employ is domain-based message authentication, reporting, and conformance (DMARC). DMARC provides email authentication the same way DNSSEC does, but at the DNS layer. DMARC is very effective in preventing email spoofing. For those familiar with how email works, you know how easy it is to make email look like its being sent from a specific brand when it’s really fraudulent. DMARC authenticates that the email is from who it says it is. It’s important to consider applying DMARC or other sender policy frameworks to your key domain names to eliminate that risk of email spoofing. All of the ongoing security monitoring needs to be proactive and continuous to ensure you are keeping up with new vital domains and security blinds spots in your approach.
We’re ready to talk
If you’d like to talk to one of our experts about a multi-layered defense-in-depth approach to your domain security, please complete this form .