by Ken Linscott
In our last post, we uncovered four vulnerabilities in DNS security, but those weren’t all the risks companies need to be aware of. There are six more threats to authoritative DNS, so that’s where we continue with this post.
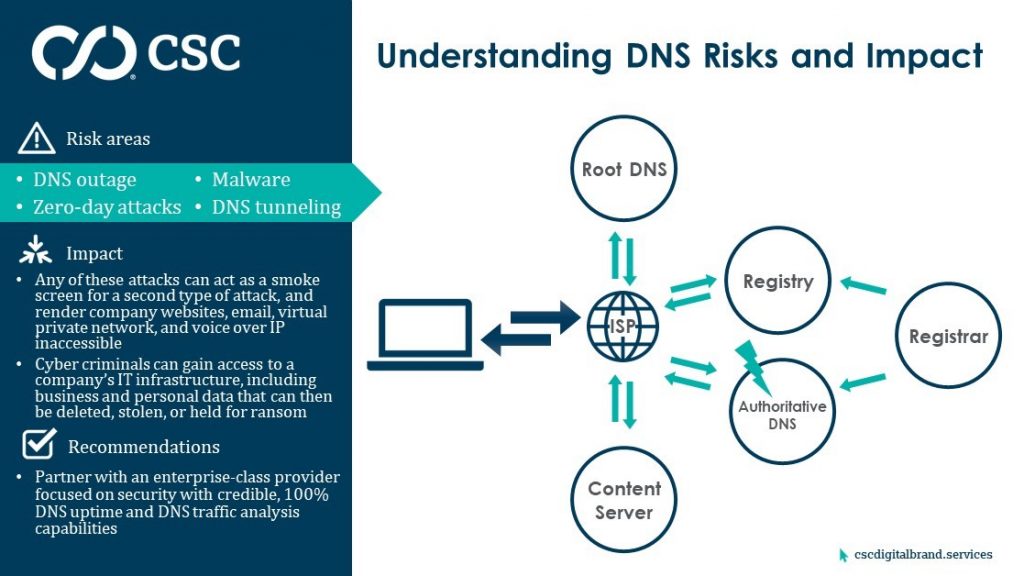
5. DNS outage
The obvious risk to any business is a DNS outage. That means the DNS a business is using does not resolve every second every day, and the business services that rely on DNS—such as websites, email, voice over IP, and virtual private networks, to name a few—are intermittent. That negatively impacts a company’s ability to operate, because in this day and age, global entities require 100% uptime.
According to International Data Corporation[1], the average total cost of unplanned application downtime is between $1.25B and $2.5B annually for Fortune 1000 companies, making the average hourly cost of an infrastructure failure about $100K, while a critical application failure is between $500K and $1M per hour.
An outage could be caused by a failure within the DNS provider’s system or process, or by a distributed denial of service (DDoS) attack against the DNS. A DDoS attack occurs when multiple systems flood the bandwidth of the targeted system resulting in failure of any related services it supports.
6. Zero-day attacks
A zero-day attack is levied against a DNS vulnerability, defect, or bug unknown to the DNS provider until hackers leverage the flaw to take it down. In the cyber world, a zero-day attack is typically accomplished using free, open-source software that allows cyber criminals to more closely examine how the targeted software works, finding the defects to exploit them.
Even when zero-day vulnerability patches are released, the majority of companies don’t implement all the patches, leaving themselves vulnerable to attack. A survey by Ponemon Institute[2] of nearly 3,000 cyber security professionals from across the globe found that 57% of breaches were due to a known vulnerability with a patch they did not apply. This is an even bigger challenge for companies running their own DNS. It’s essential that a DNS provider stays ahead of new attack vectors, test for vulnerability regularly, and exceed industry standards.
7. Malware
Malware is a general term covering different types of threats to computer safety such as viruses, spyware, worms, trojans, and ransomware. A malware attack is a cyber attack in which malicious software is covertly installed on a computer to perform activities that steal private information, confidential credentials, ruin computer systems altogether, or lock down information until a sum is paid by the affected company to restore function.
Computer systems become infected when a user clicks on a link from a phishing email, visits an infected site, downloads an infected attachment, or connects to an infected external drive. Palo Alto Networks found more than 80% of malware attacks use DNS as the primary command and control channel to avoid detection.
Most malware-generated traffic can be detected and blocked at the network level by firewalls or intrusion prevention systems. But that’s not possible for a malware attack on DNS, because DNS isn’t filtered or inspected by traffic monitoring solutions, and traffic flows freely through most networks, making it the perfect conduit for cyber crime. Recently, the increasing use of digital certificates by cyber criminals means that malware hides in fraudulent, but secure, sites—with the consumer assumption being that encrypted data is legitimate and safe.
8. DNS tunneling
DNS tunneling takes the malware attack method a step further. Tunneling encodes the data of other programs or protocols in DNS queries and responses to extract a company’s data via their own DNS infrastructure.
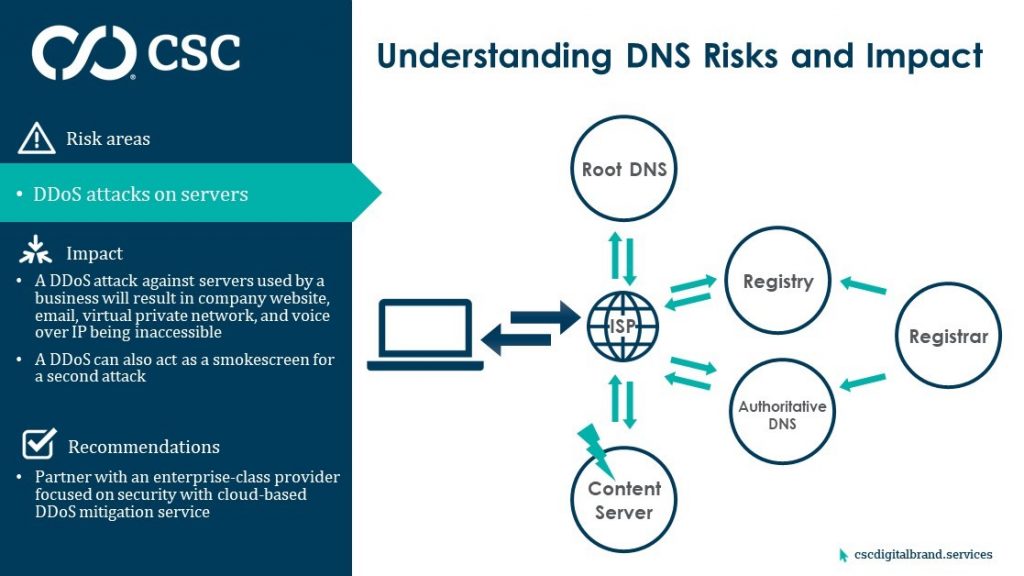
9. Distributed denial of service attacks
We’ve already covered DDoS attacks against DNS, but there is also a risk of DDoS attacks against servers running business functions like hosting a website or a database. Although not targeting your DNS, this attack would use a company’s DNS to make requests, and if successful, could take down servers involved in every step of your business.
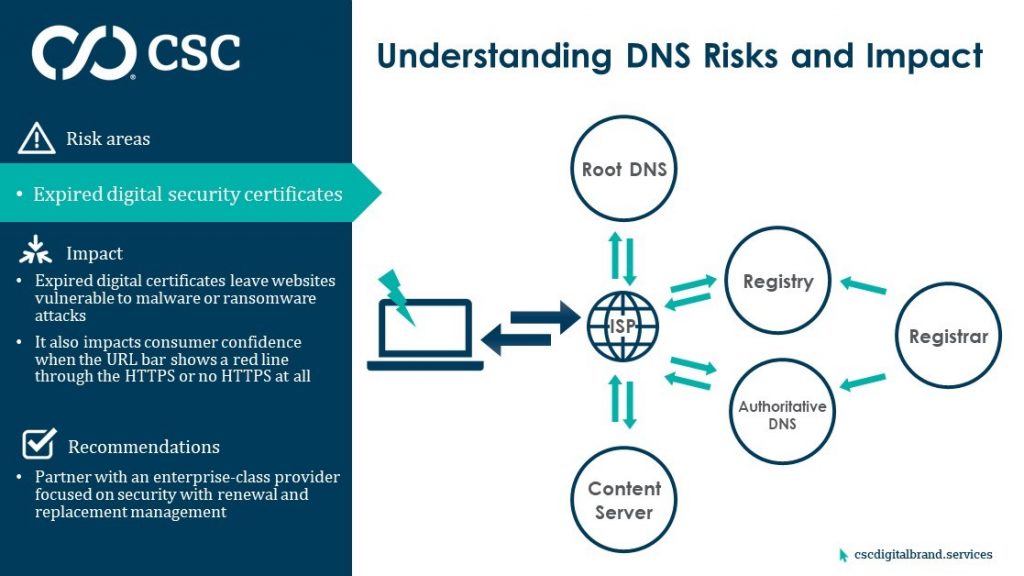
10. Poor digital certificate management
Finally, imagine visiting a website with a warning to distrust the site, or the browser disallows reaching the site at all. If everything within the DNS works perfectly, poor digital certificate management could still undermine an organization’s credibility, leave a website vulnerable to data theft resulting in audit failure and non-compliance with the EU General Data Protection Regulation, as well as other government data privacy regulations.
The complex nature of DNS means there are many vulnerabilities that can lead to DNS failing to properly support and protect a company’s online presence.
Next post
In our next post, we’ll take a deep dive into one of the biggest vulnerabilities we’ve outlined—DNS hijacking—examining the ways an attack could be launched against your business, and how to prevent it.
Subscribe to our blog to receive notification of new posts.
Read more posts in this series:
<< Part 1 – What DNS is and How it’s Vulnerable
<< Part 2 – Four DNS Vulnerabilities You Need to Know About
>> Part 4 – The Growing Threat of DNS Hijacking and Domain Shadowing
>> Part 5 – Mitigating the Risks of 10 Serious DNS Vulnerabilities
>> Part 6 – DNS Management is a Boardroom Discussion
[1 ]techrepublic.com/resource-library/whitepapers/idc-study-the-cost-of-downtime/