By Ken Linscott
In this post, we take a deep dive into DNS hijacking—as well as domain shadowing—because DNS hijacking has recently become one of the most regular and damaging cyber attacks, and domain shadowing uses similar tactics.
At the beginning of 2019, CSC joined the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, the UK National Cyber Security Centre, and other leading security organizations—including Cisco® Talos, FireEye®, and Akamai—in alerting corporations and the public to the widespread, growing threat of state-sponsored DNS hijacking.
The targets of these attacks have included government, corporate, telecommunication, and infrastructure entities—and result in website and email redirection to collect sensitive information.
DNS hijacking enables a third party to forward company customers to fake websites to steal login credentials and confidential data. This is not only a serious data risk, but a privacy nightmare, especially in light of more stringent government privacy policies, like the EU General Data Protection Regulation. DNS hijackers can also harvest information from inbound company emails, then launch sophisticated phishing attacks on customers and staff using a company’s own domains to make the attack appear legitimate.
There are three possible attack vectors used for DNS hijacking.
1. Access to the domain or DNS management portal
The first method is taking advantage of poor access and permission controls within a domain management portal. Typically, an attacker will obtain the username and password to a registrar’s portal that is not protected by two-factor authentication or IP validation, giving them access to change the name servers for domains accessible within the account, thus giving them control of the content.
2. The registrar DNS providers systems
The second possibility is that there’s a vulnerability within the registrar’s systems or processes, allowing unauthorized access. FireEye recently highlighted an ongoing domain shadowing issue for GoDaddy® that goes back to 2016, and allows attackers to access and add to the zone files of targeted domains.
3. The registry
Finally, the registry itself could be compromised. This famously played out with a Brazilian registry in 2016 when 36 Brazilian bank domains were redirected to perfectly reconstructed fake sites for six hours. The fraudulent websites even had valid digital certificates issued in the bank’s name, tricking clients whose computers were infected with malware disguised as a bank browser security plugin update. Really a Trojan, the malware was designed—ironically—to disable computer antivirus software.
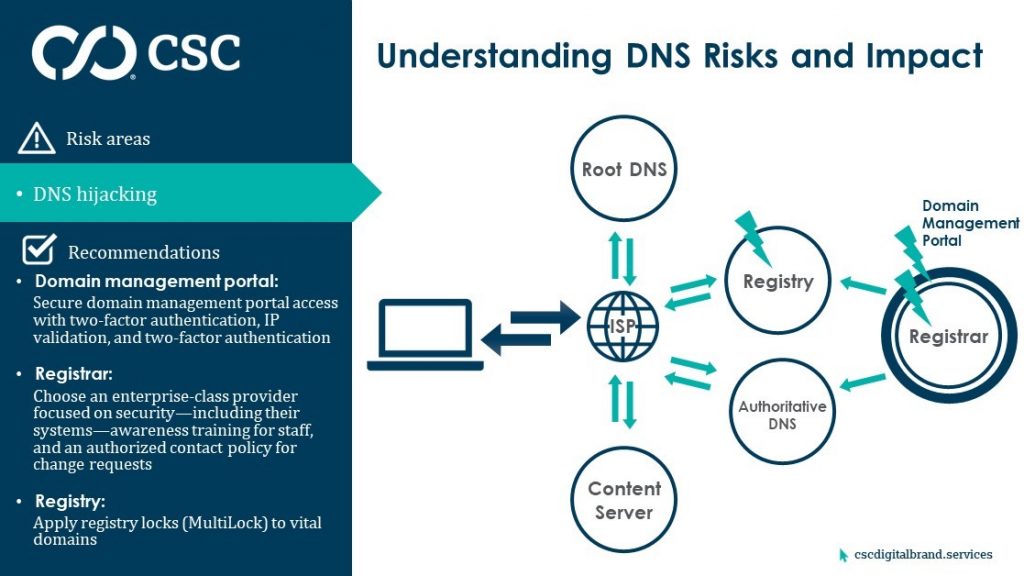
What’s clear with DNS hijacking is there’s no silver bullet to mitigate the threat. There are three distinct areas to defend and a layered approach to security is essential. We call this the Defense in Depth approach to cyber security—layering defense mechanisms to protect valuable digital assets and online data, so if one mechanism fails, another is there to mitigate an attack.
Next post
In our next post, we’ll list best practices CSC, government agencies, and The Internet Corporation for Assigned Names and Numbers (ICANN) recommend to mitigate the threats from DNS hijacking, as well as our recommendations to overcome all 10 DNS vulnerabilities.
View our webinar, DNS Hijacking: Security Learnings from the Latest Incidents.
Subscribe to our blog to receive notification of new posts.
Read more posts in this series:
<< Part 1 – What DNS is and How it’s Vulnerable
<< Part 2 – Four DNS Vulnerabilities You Need to Know About
<< Part 3 – Six More DNS Vulnerabilities That Make Security Crucial
>> Part 5 – Mitigating the Risks of 10 Serious DNS Vulnerabilities