By Ken Linscott
So far in this series, we’ve looked at the importance of DNS to online business and the 10 ways in which this infrastructure is vulnerable to cyber attack, including:
- DNS cache poisoning
- Poor domain management
- DNS hijacking
- Domain shadowing
- DNS outages
- Malware
- DNS tunneling
- Zero-day attacks
- DDoS attacks
- Poor digital certificate management
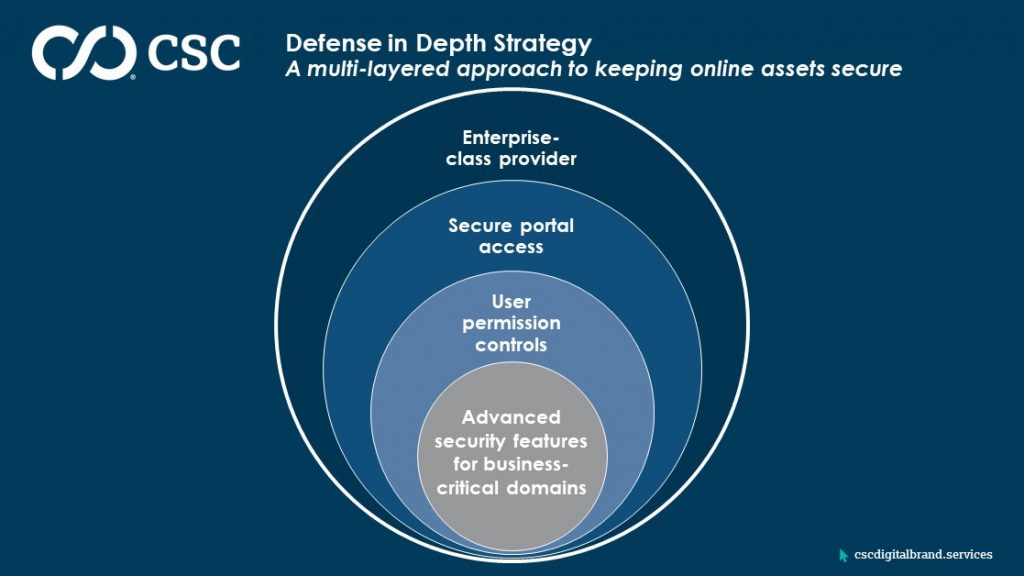
To mitigate these threats, it’s clear that a company’s defense in depth (DiD) strategy—a multi-layered approach to keeping online assets secure—should include clear policies for DNS security:
1. Employ advanced security features for business-critical domains
- Domain name system security extensions (DNSSEC) is an important tool in the overall defense of DNS vulnerabilities because it encrypts the query to the internet service provider and is also a visual deterrent for cyber criminals, as it is indicated on the WHOIS. Digitally signing the root zone means clients can be confident of reaching a company’s legitimate website; hijackers won’t be able to redirect traffic to a spoofed site designed to collect usernames and passwords.
- Registry locks stop automated changes of DNS records, preventing execution of unauthorized requests—whether it comes from compromised access to your domain portal or your registrars systems. These locks are visible in the WHOIS database, adding another deterrent criminals can see.
- Digital certificates encrypt online data to enable secure eCommerce and internet-based communications. Increasingly, every live website needs a valid, regularly renewed digital certificate to avoid being flagged by web browsers as potentially unsafe for visitors. Google®, in particular, has made it a rule to block websites without digital certificate protection.
- Domain-based message authentication, reporting, and conformance (DMARC) is an email authentication protocol that gives organizations protection against unauthorized use of their domains, commonly known as email spoofing. DMARC prevents business email compromise attacks, phishing emails, email scams, and other cyber threats.
2. Control user permissions
Companies should also routinely review permissions for staff with access to domains and the DNS portal. A good enterprise provider should be able to alert companies to changes in permissions. Only trusted individuals should have access to elevated permissions, and former employee permissions should be removed immediately. Those with elevated permission typically have access to critical DNS functions that can detrimentally disrupt or hijack a company’s online presence, including:
- Lapsing a domain
- Transferring a domain away from company ownership
- Modifying the DNS
- Editing the zone file
3. Secure DNS portal and domain access
This is far easier when domains and DNS are consolidated with one enterprise provider, which should be a trusted partner who can offer two-factor authentication (used by online banking platforms) and federated identity for a single sign on environment. These low cost yet effective protections make it harder for hijackers to access the vital company domains.
4. Consolidate with an enterprise-class domain, DNS, and digital certificate provider
When a company partners with an enterprise-class provider that’s able to manage domains, DNS, and digital certificates for large global brands, they take on the burden of monitoring and updating all the protections we’ve outlined in our blog posts—minimizing cyber threats. In the DNS space, it means choosing a provider with a credible history of providing 100% uptime to prevent DNS outages regardless of a DDoS attack.
A provider should also be able to demonstrate their investment into systems and security, including routine staff training to spot the risks for the various types of cyber attacks, because humans will always create the largest vulnerability.
The importance of selecting the right partner cannot be over stated, so we encourage companies to involve their security team in challenging potentials providers to answer in-depth information security questions.
Next post
In our next post, we address who should be responsible for implementing these policies.
Subscribe to our blog to receive notification of new posts.
Read more posts in this series:
<< Part 1 – What DNS is and How it’s Vulnerable
<< Part 2 – Four DNS Vulnerabilities You Need to Know About
<< Part 3 – Six More DNS Vulnerabilities That Make Security Crucial
<< Part 4 – The Growing Threat of DNS Hijacking and Domain Shadowing