By Vincent D’Angelo Share this post



In my recent CircleID post, DNS, Domain Names, and Certificates: The Missing Links in Most Cyber Security Risk Postures, I highlighted the significance of applying multiple layers of defense to secure online, business-critical assets. On Friday, January 24, 2020, Brian Krebs—the world-renowned cyber security journalist—reiterated the critical importance of domain name security in reference to the domain name “e-hawk.net” being stolen from its rightful owner by targeting the domain name registrar.
From my perspective, the reason for this business risk is a general lack of awareness related to domain name and DNS hijacking—and most domain name registrars do not support the registry lock protocol. However security warnings came from FireEye’s Mandiant team in early 2019 about a global DNS hijacking campaign that appeared to be connected to the Iranian government. This prompted the Department of Homeland Security to issue an emergency directive about mitigating the risk of DNS hijacking.
Cyber criminals are taking advantage of this risk and have been doing so for quite some time. Throughout 2019, Cisco Talos warned about the state-sponsored Sea Turtle attack taking control of DNS systems, and surmised that “the actor ultimately intended to steal credentials to gain access to networks and systems of interest.” And just this week, Reuters reported “Exclusive: Hackers acting in Turkey’s interests believed to be behind recent cyberattacks – sources” that another group of hackers alleged to be working for the Turkish government’s interests attacked government organizations and companies via DNS hijacking.
In his story, Does Your Domain Have a Registry Lock?, Krebs walks through measures companies implement to protect their vital domain names. He also states that the majority of organizations—regardless of industry or geographic location, including the Forbes Global 2000—are at risk, because less than 25% of companies have adopted the registry lock protocol.
Best practices to maximize security against domain name and DNS hijacking*
- Use registration features like registry lock to protect domain name records from being changed. Note: this will increase the time it takes to make changes to your locked domain.
- Use DNS security extensions (DNSSEC), both signing zones and validating responses.
- Use access control lists for applications, internet traffic, and monitoring.
- Use two-factor authentication, and require it to be used by all relevant users and subcontractors.
- Choose unique passwords and consider using a password manager.
- Review the security of existing accounts with all providers, and make sure you have multiple notifications in place for when a domain you own is about to expire.
- Monitor the issuance of new digital certificates for your domains; keep track through certificate transparency logs, for example.
Furthermore, domain name registrars have varied controls, processes, and security measures. When assessing your domain name registrar’s capabilities, validate they’re applying a defense-in-depth approach to secure your vital domain names.
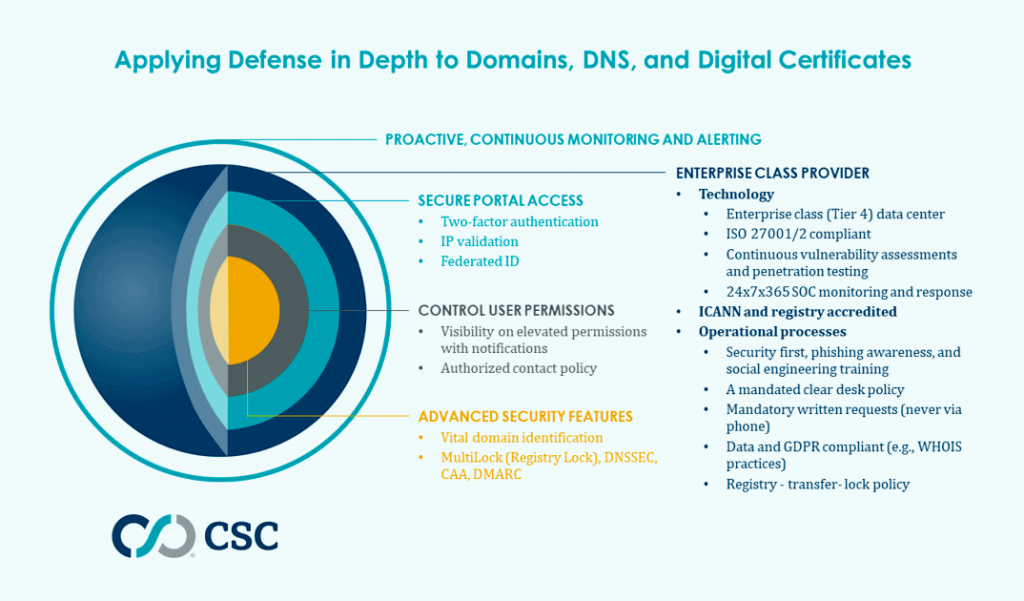
- Are they Internet Corporation for Assigned Name and Numbers (ICANN) and registry accredited with enterprise-class technology and operations processes?
- Do they provide secure portal access with two-factor authentication?
- Do they help apply advanced security features like registry lock, DNSSEC, domain-based message authentication reporting and conformance (DMARC), and certification authority authorization (CAA) records?
- Do they allow for the control of user permissions?
- Do they help identify vital domain names and provide continuous monitoring and alerting?
Ask your domain name registrar these tough questions because they hold the “keys to the kingdom,” which if not secured properly, can jeopardize your company’s reputation, finances, security, data, and intellectual property.
*Source: krebsonsecurity.com/2020/01/does-your-domain-have-a-registry-lock/