In CSC’s recent insight paper, we address the trend that many business leaders today don’t realize the extent to which their modern enterprise—and its millions of digital assets—rely on. It’s a vast domain ecosystem that needs to be protected from online threats. Often, to better understand this need for domain security, we need to understand how critical and interconnected domains are within a business.
Domains, in many ways, are a gateway to your digital ecosystem.
Like the sun of our own Milky Way, some domains are absolutely vital to sustaining the ecosystem because they’re the source of critical business infrastructure—like websites, emails, service applications, and client, supplier, or partner portals. Then there are domains or subdomains created for temporary initiatives, like marketing campaigns, that are no longer needed after a certain period of time. Companies may also register lookalike or “homoglyph” domains that resemble legitimate ones as a defense mechanism to avoid malicious third parties buying and exploiting their affiliation with the brand.
Galactic storms
Cybercriminals know the value of domains and are perpetually scouring the internet for opportunities to exploit them, so it’s crucial to understand how these malicious actors seek to obtain and leverage fraudulent ones.
There are numerous ways that unprotected domains could be acquired and weaponized, for instance:
- Legitimate domains or subdomains abandoned by a company, or improperly configured domain name system (DNS) records, can be hijacked to redirect traffic to malicious sites.
- Lapsed domains not re-registered by the brand itself can be re-registered by third parties with malintent.
- Malicious third parties may register a domain and leave it dormant—inactive and unsuspicious—until an attack is launched at a later time.
- Attackers may register lookalike domains from consumer-grade registers for fraudulent behavior.
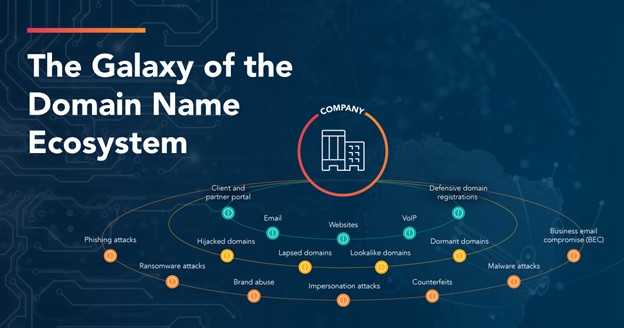
But usually, it doesn’t stop there. Individual domains maliciously registered by cybercriminals are often the precursor to more sophisticated threat operations like ransomware, malware, phishing, brand impersonation or abuse, business email compromise (BEC), brand counterfeit, and more.
Recommendations for universal protection
For all the time and money businesses put into building trusted brands, it’s a shame that trust can be gone in an instant if a company falls victim to online crime. That’s why it’s incredibly important to have full visibility and control over your domains to prevent malicious domain activity from reaching the core of your business’ infrastructure and disrupting critical operations.
By implementing an online brand protection program with domain monitoring and enforcement mechanisms, businesses can more effectively secure their domain “galaxies,” remove fraudulent content, prevent initial exploitation, and stop malicious activity before it begins.
At CSC, we’re committed to educating enterprises on domain security best practices and equipping teams with the right resources to protect their brand against the cyber threats that aim to exploit them.
If you’d like to learn more about how to secure the galaxy of your domain ecosystem, download our latest insight paper, “The Intersection of Your Cybersecurity Posture with Domain Name Management.”
