Although the Olympic games have yet to transcend to the digital realm and include internet-based sports, the online arena still poses a significant threat to world events like the Olympics that are always targeted by bad actors and fraudsters. From counterfeit items to fake tickets, to phishing scams, bad actors will be using the Olympics’ worldwide status and recognition to dupe people.
As a starting point to an extensive catalogue of avenues for exploitation at the Paris Olympics, brands and domain names will primarily be used in cyberattack campaigns, impersonations, fraud scams, and brand counterfeiting. Monitoring domain ecosystems globally—such as domain names that are look-a-like, dropped, re-registered, or newly registered—should be at the forefront of any corporate security posture and brand’s online strategy toward mitigating these digital threats.
As the Paris 2024 Olympic games draw near, CSC has undertaken research into domain name behaviors surrounding the games and has detected a surge of domain activity. Using CSC’s 3D Domain Security and Enforcement product that is powered by the one-of-a-kind DomainSecSM platform that harnesses Machine Learning Deep Search (MLDS) technology, we’ve examined this activity in succinct detail to fully understand the extent of the recent domain name activities and conducted trend analysis. In short, we’ve removed any hurdles—pun intended—in understanding domain behavior that may put major brands at risk during this season’s Olympic games.
What we found
We identified over 8,087 domain names in relation to the term “Olympic” within the past 12 months. A total of 7,568 domain names were registered within generic top-level domains (gTLDs) and 509 domain names within country code top-level domains (ccTLDs). The distribution within gTLDs was: .COM received 4,806, .ORG received 483, and .NET 203. Moreover, interesting extensions such as .ONLINE received 203, .XYZ received 145, .SITE received 104, .SHOP received 102, and .GAMES received 29. Drilling down further using the search term “paris2024,” we uncovered more than 400 domain events within the same timeframe—a high number compared with other branded results, and roughly in line with what we’d expect to see from other world events of this type.
As CSC’s 3D Domain Security and Enforcement technology uses unique search models such as homophones, fuzzy matches, and homoglyphs, results are not limited to the parameters of identical domain name matches, and we can view the domain name ecosystem in its entirety. This means we were able to uncover results like “pares2024.org” (typo and homophone) and “pÃ¥ris2024.org” (homoglyph)—tactics frequently used by bad actors, indicating a potential to launch fraudulent campaigns. Furthermore, 3D technology also allows us to view results using language variations of “olympic.” Using these search parameters, we were able to broaden our search further, finding more than 30 domain events with the keywords “olympic,” “olympique” (French), “olympie” (Czech), or “olimpic” (Romanian) used in combination with the original search term “paris2024.”
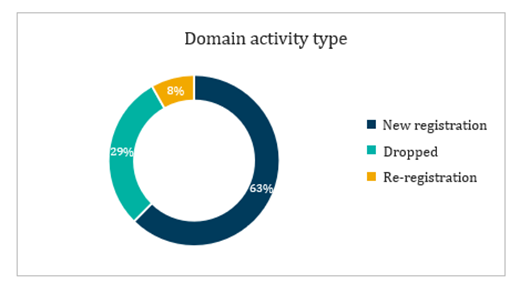
Figure 1 above shows that 63% of the domains with the key term “paris2024” are newly registered domains, 29% of those names registered within the year had been dropped, and 8% re-registered. Companies defensively register critically important domain names to prevent online fraud but for various reasons, they decide to drop domains, or let them lapse. Cybercriminals wait for this to happen and immediately re-register the same domain name for malicious purposes. They’re constantly on the lookout for available, branded domains they can weaponize.
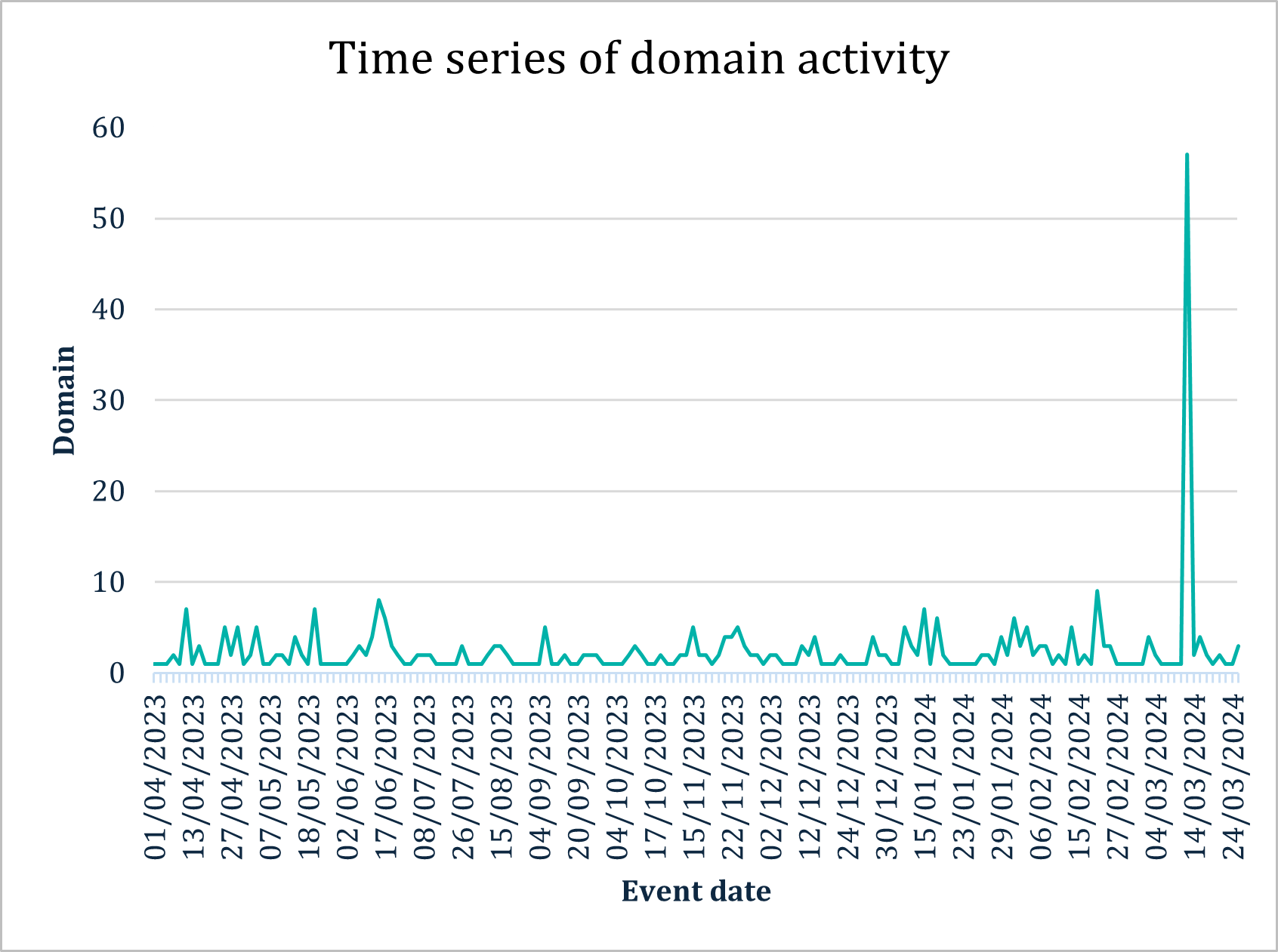
Further scrutiny of the domain name datasets revealed an outlier, detected on March 12, 2024. As Figure 2 shows, over 55 domain registrations took place that day using variations of “paris2024.org.” Such data spikes are significant as they follow the patterns of fraudulent campaigns that are launched at a later time by bad actors. Further analysis has determined that these domains all presently resolve to parking pages with sponsored links, use a matching registrar, and include identical A Records (in some cases). Moreover, since the same hacked infrastructure is being used to launch future fraudulent campaigns, it’s a clear indication that the same bad actors are behind such domain name registrations. Finding these kinds of trends in data is paramount in understanding the movement of the domain name landscape and identifying any potential threat vectors.
Also in our analysis, we uncovered a subset of approximately 15 domains referencing sponsors of the Paris Olympics with the core search term “Paris 2024.” We advise brand owners that are sponsors of large world events like this to add keyword strings related to the event to their daily domain name monitoring programs.
Finally, from the identified domains, we detected the highest volume of domain registrations relating to Paris 2024 for the .COM TLD. This was followed by .ORG and .FR in silver (second highest volume) and bronze (third highest volume) places. All these factors are critical in analyzing any potential domain name threat vectors related to the upcoming Olympics, as they assist our understanding of whether the intention behind the domain name registration is legitimate or not.
Further analysis
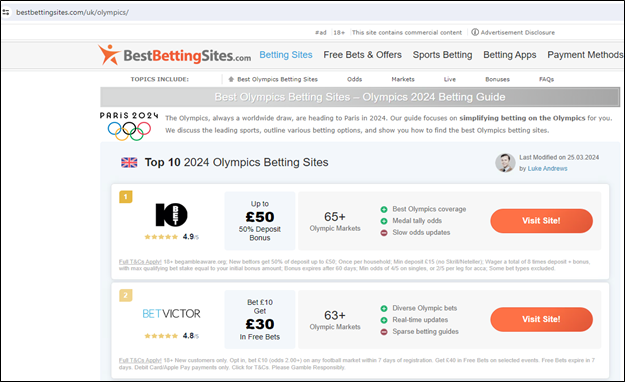
A deeper domain name analysis is used to determine whether a domain name is dormant or fraudulent. A dormant domain name is defined as one that is not weaponized with a type of threat vector while a fraudulent domain name is one that has been weaponized with a threat vector, such as phishing or malware. Domain names registered with mal-intent include: domains with a risk level of the secure sockets layer (SSL) certificate used, domain MX records detected, domain keyword, web page content analysis, and proxy services used, shady hosting provider or registrars used, and many other potential indicators of compromise. For example, the re-registration of the domain “paris2024.media”—which currently redirects to “bestbettingsites.com” and features Olympic games branding (Figure 3)—was uncovered by assessing the risk profile of the SSL certificate, which flagged a need for further deeper analysis. Moreover, dormant domain names that don’t resolve to any content, but have active MX records (e.g., olympicgamesparis2024.shop) are also of vital importance in analysis. The presence of MX records on a domain can indicate that it may be weaponized in the future for a phishing or malware campaign, or other fraudulent activity.
What are the takeaways for brand owners?
Our analysis identified a large number of domain events using “Olympic” within the past 12 months, plus 400 including the keyword “paris2024,” and 30 using language variations. But what can brand owners take from what we found?
- Search far, search wide. It’s vitally important for brands to be able to do a full and comprehensive search of the complete daily global domain name ecosystem within gTLDs and ccTLDs. Basic domain monitoring searches may be able to identify a few domain event types (e.g., exact matches, wildcards, typos), but not worldwide. Using a monitoring service like CSC’s 3D Domain Security and Enforcement solution, we can detect a much wider number of domain name ecosystems by undertaking searches for additional domain variations on top of what a basic search would provide. By having the full picture, brand owners can better understand what their digital landscape looks like, and then take informed action as and when needed.
- Detection: include keywords in searches. It might be a basic point, but you need to use vendors who can search domain names globally in real time across gTLDs and ccTLDs. For example, without including the keyword “paris2024” in our searches in our domain name data lake, we wouldn’t have uncovered sites such as that in Figure 3 that redirected to gambling content. Unless you’re a gambling brand, association with gambling or other adult content might not be a desirable one. If your brand sponsors any events, make sure the event name is a keyword search that you include as part of your monitoring program.
- Deep search and analysis: As brand owners find suspicious domain names, further investigation is mandatory to analyze the associated potential threat vectors. This is done by having automated tools that can determine the state of the domain name as dormant or fraudulent.
- Comprehensive enforcement: Have a partner execute takedowns on phishing or malware downloader sites, typosquatting domains, search engine SEO sites, and social media portals, and remove of marketplaces (fake, copycat) counterfeit products or website content.
- Continuous automated monitoring: After detecting dormant domain names or conducting a takedown on threat vectors, it’s crucial to have automated monitoring tools capable of continuous monitoring for any domain that may resurface or get weaponized by bad actors. Moreover, the tools must guard against blocking techniques used by bad actors.
If you’d like to gain further insights into your domain portfolio, complete our contact form.
