A key requirement for a bad actor wanting to launch a brand attack is the registration of a carefully chosen domain name. The most convincing infringements frequently use a domain name that’s deceptively similar to that of the official site of the target brand. This allows a variety of attacks to be executed, including phishing attacks—where the domain is used to host a lookalike site or produce a deceptive sender address for emails—and other kinds of brand infringement where users are misdirected to fake sites via mistyped URLs or search engine manipulation.
One well established threat vector used in creating fraudulent websites is the use of strings like “www” or “http” within the domain name itself—e.g., registering domains such as www-google.com or httpgoogle.com to impersonate the legitimate site (i.e., www.google.com or http://google.com).
CSC carried out a study in August 2022 using its 3D Domain Monitoring technology to consider patterns of activity in domain registrations for names beginning with “www” or “http” over the preceding one-year period. The analysis includes identification of newly registered domains (N), re-registered domains (R) or dropped (i.e., lapsed) domains (D). Each instance of these activities for a particular domain is referred to as an “event.”
Findings
Between August 2021 and August 2022, more than 230,000 events were identified for “www” domains, and more than 12,000 for “http” domains. Figure 1 shows the continuous activity across the one-year period, with numerous peaks and troughs.
.jpg)
Among the full dataset, a number of specific keyword strings were found to appear as the second-level domain names (the part of the domain name to the left of the dot) multiple times. They represent either repeated lapses and re-registrations of particular domain names, or the registration of distinct domains with the same second-level domain name but different top-level domain (TLD) extensions—so-called “cousin” domains. Of these keyword strings, several referenced well known brand names, or variations or typos of those names, indicating an intention to target the brand in question, as shown in Tables 1 and 2.
| Keyword string | No. registration or drop events |
| www-roblox | 21 |
| www-lcloud | 16 |
| www-apple | 15 |
| wwwgoogle | 13 |
| www-avito | 12 |
| www-citizens | 11 |
| www-yandex | 10 |
| www-torproject | 10 |
| www-icloud | 10 |
| www-blablacar | 10 |
| www-bitstamp | 10 |
| www1royalbank | 10 |
| Keyword string | No. registration or drop events |
| https-skinbaron | 9 |
| https-www-ruraivla-com-lsum-main | 8 |
| httpsgoogle | 7 |
| https-csmoney | 7 |
| httpgoogle | 7 |
| http18comic | 7 |
| httpsstreamlabs | 6 |
| https-googlecom | 6 |
| https-httpsgoogle | 6 |
| httpsgoogledotcom | 6 |
| httpsgoogleplay | 6 |
| https–google | 6 |
| httpsgoogle-com | 6 |
| httpsgooglecom | 6 |
| httpsecuregoogle | 6 |
| httpsdealersvwcredit | 6 |
| https-anydesk | 6 |
| httpqgoogle | 6 |
| httpagoogle | 6 |
| httpcredito-app-nubank | 6 |
| http2google | 6 |
Tables 3 and 4 show the top TLDs represented within the dataset.
| TLD | No. registration or drop events |
| .COM | 204,795 |
| .XYZ | 6,233 |
| .NET | 4,411 |
| .ORG | 3,008 |
| .TOP | 1,646 |
| .VIP | 1,423 |
| .INFO | 950 |
| .FR | 937 |
| .ONLINE | 714 |
| .UK | 676 |
| TLD | No. registration or drop events |
| .COM | 8,284 |
| .XYZ | 1,267 |
| .NET | 429 |
| .ORG | 388 |
| .LIVE | 228 |
| .ONLINE | 180 |
| .INFO | 170 |
| .UK | 160 |
| .FR | 154 |
| .SITE | 150 |
Unsurprisingly, .COM dominates the dataset, reflecting both the continued popularity of the TLD, and its extensive use in official domain names of the brands being impersonated. However, a range of new generic TLDs (gTLDs) such as .XYZ, .TOP, .VIP, .ONLINE, .LIVE, and .SITE also feature in the lists, consistent with previous observations that these extensions are popular with fraudsters[1],[2],[3].
Infringements targeting top brands
CSC also analysed the frequency of registration and drop events for “www” and “http” domains names incorporating any of the top 10 most valuable company brands in 2022[4], on the assumption that these are likely to be attractive targets for bad actors. The findings are shown in Table 5.
| Brand string | No. registration or drop events for “www” domains | No. registration or drop events for “http” domains |
| apple | 212 | 43 |
| 143 | 120 | |
| amazon | 114 | 19 |
| microsoft | 14 | 6 |
| tencent | 0 | 0 |
| mcdonalds | 8 | 2 |
| visa | 58 | 10 |
| 38 | 31 | |
| alibaba | 7 | 4 |
| vuitton | 1 | 0 |
| TOTALS | 595 | 235 |
The associated keywords also present in the domain names may give further insight into the intentions of those registering the domains. For example, in the dataset of 255 “apple” domain events, we frequently see certain keywords, their variants or misspellings, that may indicate phishing activity, including “login” (13 instances), “support” (47) and “activate” (17).
Significantly, of the 564 active, unique domains containing any of the top 10 brand names taken from the dataset above, 16% feature active MX records, meaning they’re configured to send or receive emails, another indicator that they may have been registered for use in phishing campaigns.
Looking at the content of the websites among the brand specific dataset, the majority of domains were inactive by the time of analysis, although several had been flagged as dangerous or deceptive at the browser level, suggesting they may have previously hosted fraudulent sites. Others included pay-per-click links, monetizing the misdirected web traffic attracted to these sites, and potentially driving users to competitor sites. Some of the sites also display banner advertisements to gambling-related or adult sites. Figure 2 shows three examples of websites found to feature live, infringing content.
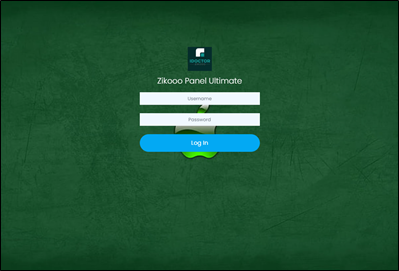
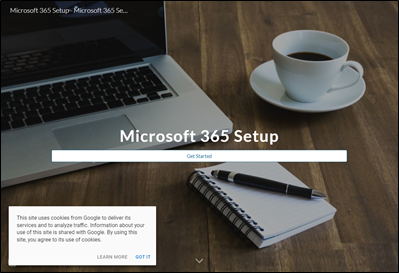
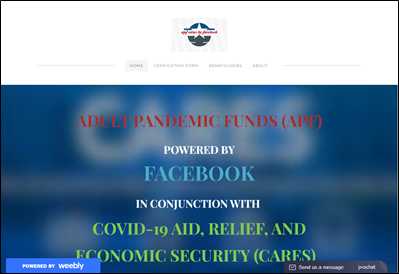
Conclusions
Over one year, CSC’s 3D Domain Monitoring technology identified nearly a quarter of a million registration or drop events of domains designed to be deliberately deceptive, by virtue of the inclusion of the strings “www” or “http” at the start. A significant proportion of these appear to target specific brands, with 830 of the events corresponding to just the 10 most valuable brands.
Several domains were found to resolve (or previously resolved) to infringing content, while 16% of the domains relating to the 10 most valuable brands were configured with active MX records. This indicates they may have been registered for their email function—an indicator of possible phishing campaigns.
These findings highlight the importance of brand owners employing an active domain monitoring and enforcement program. CSC’s 3D Domain Monitoring technology can detect the registration, re-registration, and dropping of domain names containing brand terms and other keywords of interest—including variants like fuzzy matches and character replacements—across a wide range of extensions. This enables brand owners to identify and mediate the risks associated with infringing third-party domain registration activity.
If you’d like to find out more about CSC’s 3D Domain Monitoring and Enforcement services, please complete our contact form to speak to one of our specialists.
[1] cscdbs.com/blog/branded-domains-are-the-focal-point-of-many-phishing-attacks/
[2] circleid.com/posts/20210908-credential-hinting-domain-names-a-phishing-lure
[3] unit42.paloaltonetworks.com/top-level-domains-cybercrime/
