by Ken Linscott
The domain name system—or DNS—is the infrastructure behind the internet. Technology professionals know DNS is the fundamental building block for every company’s online presence.
Websites each have a unique numeric internet protocol (IP) address, and DNS translates human-friendly web site names into IP addresses that are easier for computers to manage.
In this first installment of our DNS blog series, we explore how regardless of the type of business, reliable DNS is instrumental in a brand’s online presence, is tied to online business success, and can also help prevent cyber attacks. Keep reading to also find out exactly how DNS works.
Reliable DNS = brand success and customer trust
The holy grail for DNS is reliable uptime. The problem for businesses lies in vulnerable DNS, which opens up a whole host of cyber risks, as well as the associated costs to mitigate the problems that result from vulnerable DNS.
Recent cyber attacks highlight specific techniques bad actors use to intercept and manipulate a company’s legitimate web traffic, harvest information like credentials or email addresses, and perform other malicious activities, such as phishing. In some cases, free digital security certificates—that require low validation—were used to increase the credibility of the scams, compounding the issue for brands and customers. Consumers are weary of their personal information being accessible to and stolen by criminals, thus breaches hurt the reputation and bottom line of companies around the globe.
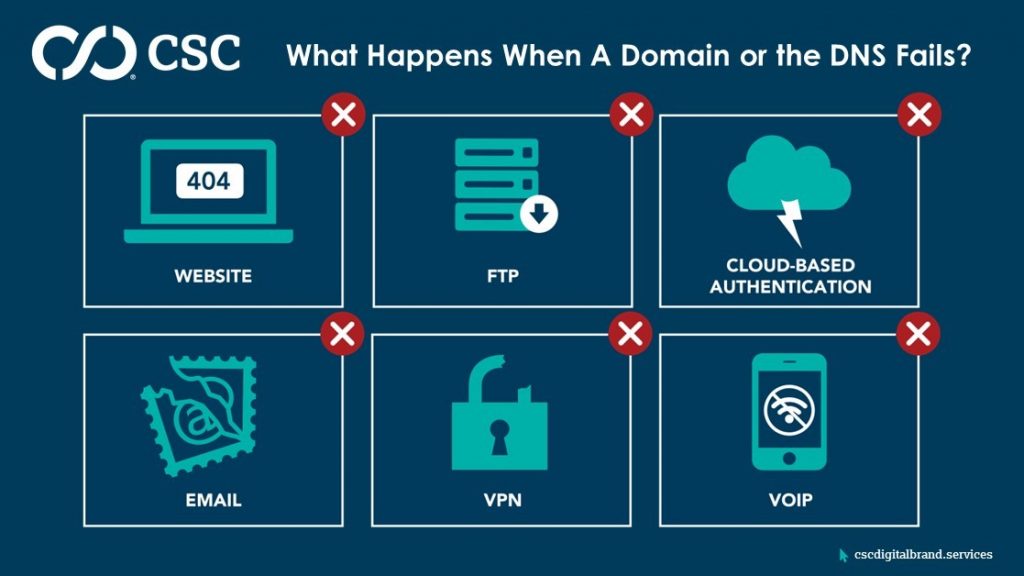
If DNS fails, customers attempting to visit a website simply will not reach their destination. Nor will employees be able to send or receive company email. If a company relies on voice over IP to make and receive phone calls, access is cut off if DNS goes down, and companies will have to resort to using landlines and mobile devices to reach customers. Lastly, the ability for remote employees to access systems via virtual private network will evaporate, inevitably leaving a company short staffed at the exact time it needs all hands on deck.
How DNS works
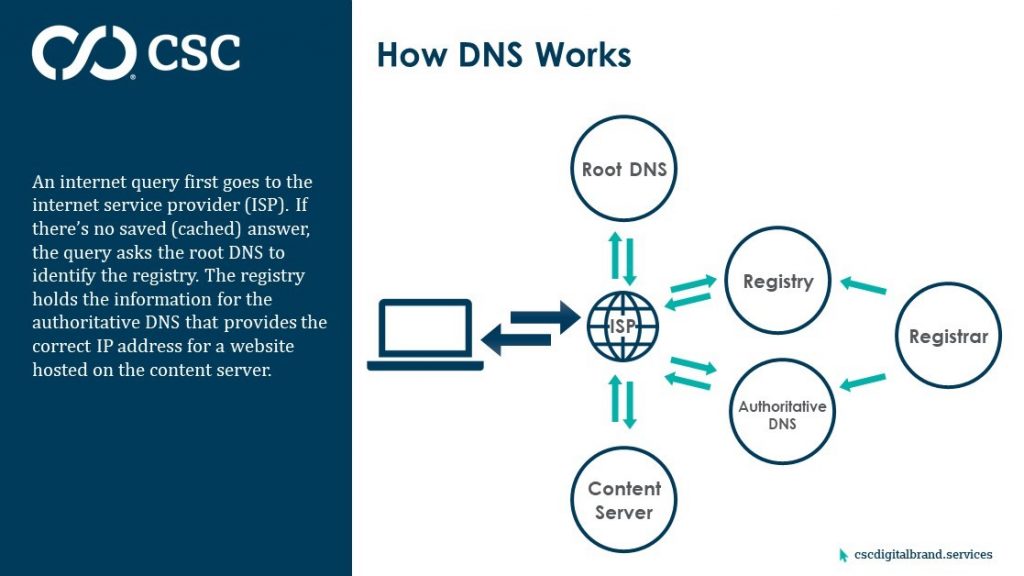
Internet queries first go to the internet service provider (ISP), and if the
ISP has the IP address cached, the computer will resolve to the right location.
If the ISP doesn’t have the IP address cached, it will query the root DNS to
ask it which registry to visit. That registry tells computers which
authoritative DNS holds the answer to where the content is.
This is a complex journey, which usually happens in the blink of an eye with no issues whatsoever. However, it’s that complexity—and the multiple points of possible failure in particular—that enables attackers to compromise the process and steal or redirect traffic to fraudulent websites.
Next post
In our next post, we’ll detail five DNS vulnerabilities bad actors target.
Subscribe to our blog to receive notification of new posts.
Read more posts in this series:
>> Part 2 – Four DNS Vulnerabilities You Need to Know About
>> Part 3 – Six More DNS Vulnerabilities That Make Security Crucial
>> Part 4 – The Growing Threat of DNS Hijacking and Domain Shadowing
>> Part 5 – Mitigating the Risks of 10 Serious DNS Vulnerabilities